The coronavirus disease 2019 pandemic has hindered performance for many organizations and agencies. Businesses are operating in a new, more digital way. That’s why organizations of all sizes want to develop their own personal data protection systems that support the Personal Data Protection Act (PDPA) of 2019 in response to the new normal model. It needs to be robust, comprehensive, a standardized approach that makes it easy to get started. easy to manage, worth the investment
Fortinet recommends that organizations begin with a risk assessment by referring to the Thailand Data Protection Guidelines V3.0 extension in the Faculty of Law. Chulalongkorn University has prepared and published guidelines on how Thailand can raise standards for personal data protection to be acceptable.
Risk assessment in the document is an activity that helps to formulate measures to maintain security in three areas: confidentiality of information. (privacy), integrity (integrity) and availability. (availability) to achieve its risk level by assessing the likelihood of a hazard occurring when assessing its impact, which may be high, medium or low, so it may consider the purchase of personnel, processes and technology or equipment could. In each Appropriate Equipment Area Security Officer (CISO) will determine such policies in conjunction with security personnel.
From the above risk assessment results, small and medium enterprises can choose to manage their risks by mitigating risks. They may consider using security procedures to help manage the risk, such as clearly defining the use of user accounts with high privileges. and is limited to those who only need to use it, including in compliance with specific business requirements. Other parameters include consideration of control measures.
After the organization has assessed the security risks of personal data. Organizations will be able to define security measures related to organizational management. (Organization Security Measures) and Appropriate Technical Security Measures (Technical Security Measures). Examples of security control measures related to organizational management, such as security management, include the formulation of relevant policies and procedures. Duties and Responsibilities Incident Response and Business Continuity Management It is to determine control measures in the event or occurrence of a personal data breach. and human resource management, including how the organization must communicate its responsibilities with respect to the confidentiality of personal data and ongoing training.
For technical safety control measures, the 9 important areas are as follows:
1. Access Control and Authentication – Access control and authentication to prevent unauthorized access to information systems used to process personal data. Control measures that can be implemented, such as 2-factor authentication (2FA), etc., are for high-risk organizations.
2. Logging and Monitoring – Event log and user activity monitoring. To be used as evidence in the event of any unauthorized access, use, alteration or modification.
3. Easy Data Protection – Security of stored data. Data encryption in machines such as computers and servers, including database systems where personal information is stored, etc.
4. Network/Communication Security – Network security is important. This includes external connections (such as the Internet) and connections to other systems (both internal and external). There should be network-level security tools such as firewalls, IPS devices, and NACs, including encryption. Externally sent information is also important.
5. Back-up – Backup is an activity that allows an organization to recover corrupted data. For high-risk organizations, more frequent backups should be considered. And also encrypts the data stored in the backup device etc.
6. Mobile/Portable Devices – Preventing risks from mobile devices such as smartphones or tablets by verifying your identity before using the device. And encrypt personal data on mobile devices etc.
7. Application Lifestyle Security – Organizations should consider achieving security throughout the application development lifecycle, such as penetration testing of applications and related systems. And there is a process of evaluating patch testing before installing patches etc.
8. Deletion/disposal of data – Organizations must take measures to delete or destroy personal data to make it irreversible. For example, it must be overwritten multiple times and destroy the storage device.
9. Physical Security – Physical security which includes the installation of an intrusion alarm system in an area requiring high security.
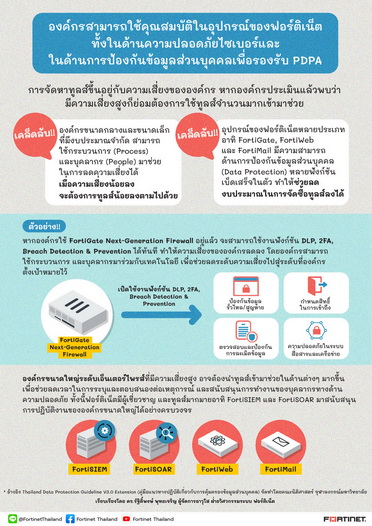
The frequently asked question is what additional equipment or technologies do organizations need to purchase? The answer is that the purchase of equipment depends on the organization’s own risk. The higher the risk, the more organizations will need tools to assist. For small and medium-sized organizations with limited budgets, process(s) and people(s) can help reduce risk. When the risk is low, the equipment required will also be less. If the organization uses Fortinet’s security tools (security) to secure the act. Many Fortinet tools, such as FortiGate, FortiWeb, or FortiMail, have data protection capabilities, having cybersecurity or already complying with the NIST, ENISA, ISO27001 framework. This will enable organizations to reduce their level of security risks and reduce their budget for equipment purchases.
For example, if the customer is already using the FortiGate next-generation firewall, the customer can enable instant DLP, 2FA, breach prevention functions, etc. The risk to the organization will be reduced. The organization aims to reduce risk to an acceptable point by using technology, processes, and personnel to help reduce risk.
On the other hand, if it is a large enterprise with high risk, more equipment may be needed to help reduce the time taken to identify and respond to incidents. Including helping to support the work of overloaded security personnel Fortinet offers tools such as FortiSIEM, FortiSOAR and other technologies. To strengthen and accelerate large enterprises in the field of data protection.
The cabinet, however, resolved to enhance the enforcement of the Act. The Personal Data Protection Act 2019 has been moved to June 1, 2022, but the impact and damage to our business and corporate reputation is priceless. Organizations therefore need to accelerate the completion of the PDPA solutions that Fortinet can bring to its experience. Expertise and globally proven solutions to help organizations meet personal data protection laws for all types of businesses.